How your computer gets hacked by sneaky Trojans/Backdoor
We had a customer coming with infected laptop last month and the laptop was actually remotely controlled by the cybercriminal without her awareness. She didn't know how this happened, but after analyzing her recent activities, she realized it was just an email sent from the "friend".
Here is a demonstration how the Trojans get into our Windows computers by emails.
An email came in this morning declaring "Remittance copy from bank". I was interested in this kind of emails while expecting some payments.
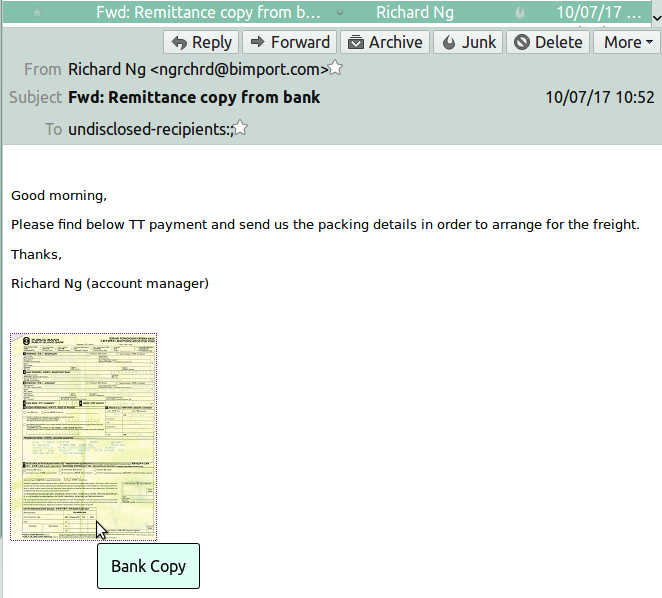
The attachment looked all right like a screenshot or pdf file. It asked me to save or open when I clicked the picture. However, the PDF file didn't look normal.
Bank-Copy_7367473839933_pdf.jar is not a PDF file, it's a java program.
A PDF should be like this: Bank-Copy_7367473839933.pdf not Bank-Copy_7367473839933_pdf.jar

Your AntiVirus program might warn you if you have a good one. However, some AntiVirus programs might miss the new viruses, in which case, you would probably click "open it". Then nothing happens, however, the Trojan is starting to do its evil in the background if you have java runtime installed. The fact is most computers would have java runtime in the system to be able to run certain programs/services.
I don't have AntiVirus program on my production computer as I don't use Windows myself. So I saved the file (with Trojan) and transferred to a Windows 7 machine.
Let's go further to have a look at how this Trojan worked. You don't need fancy tools to do this, just some Windows built-in command. Open a command line terminal by clicking Start -> run -> cmd.exe, then type in netstat -an 2 to monitor the open ports, hen execute the Trojan file. Here we see the Trojan was trying to connect to remote server.
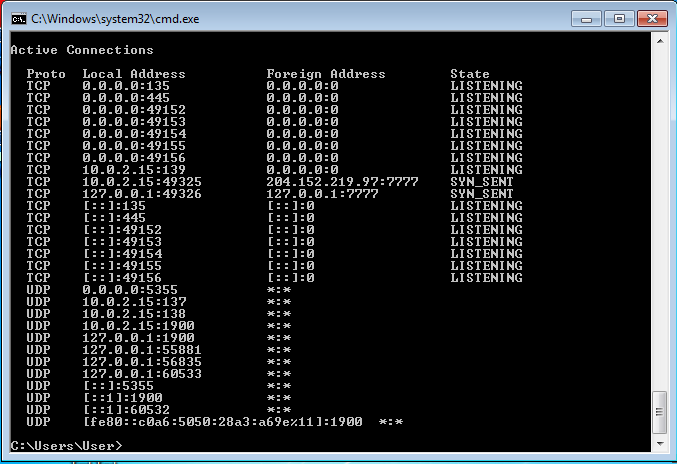
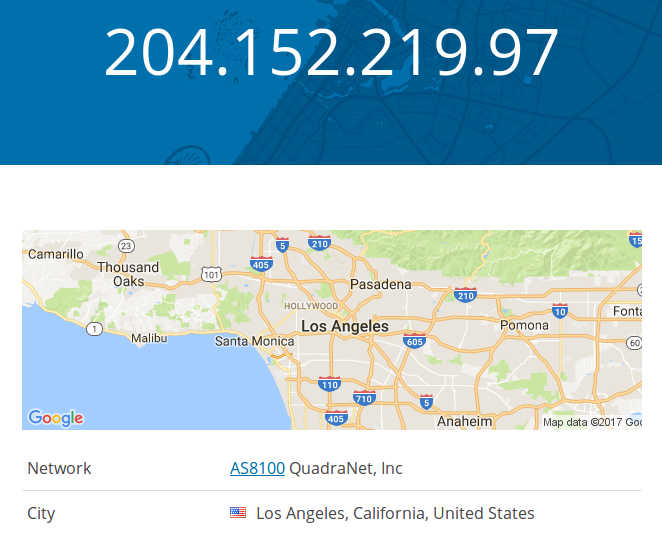
10.0.2.15 is my local IP address and 204.152.219.97 is the remote address, and :7777 is the port. If you check the IP address location, you will find out it's in the US.
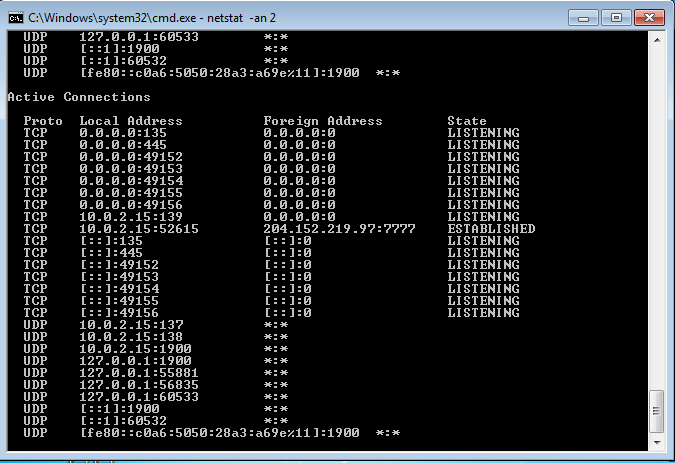
After a while, the compromised Windows 7 was established connection with remote server. Don't be surprised if you see the mouse cursor moving around even you haven't touch it. It has been remotely controlled by the cybercriminals.
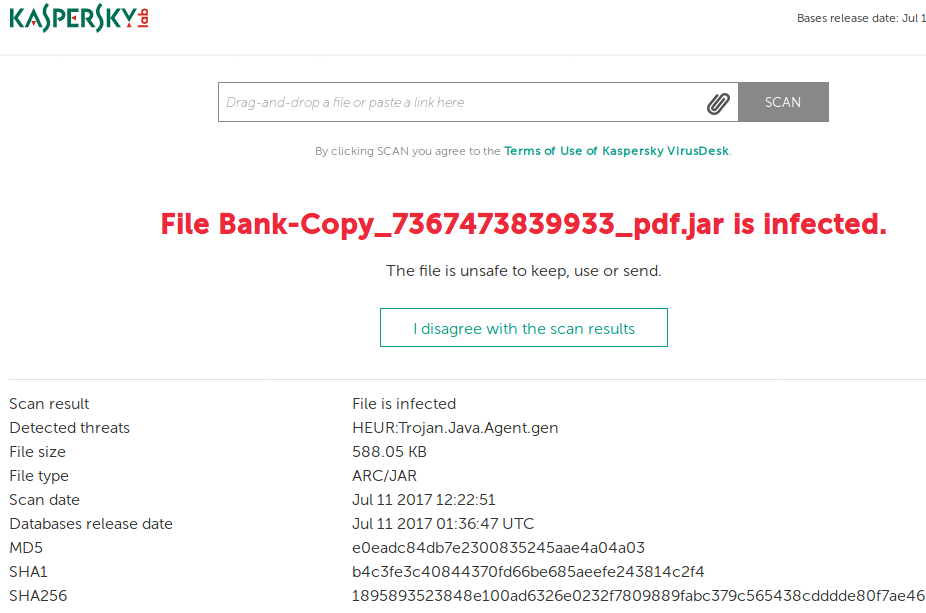
Don't just open the email attachment if you have any doubt. There are heaps on-line virus sample analysis service, Kaspersky VirusDesk(https://virusdesk.kaspersky.com/), Microsoft Malware Protection Center, VirusTotal - Free Online Virus, Malware and URL Scanner(https://www.virustotal.com/), name a few.
Here is a screenshot from Kaspersky VirusDesk.
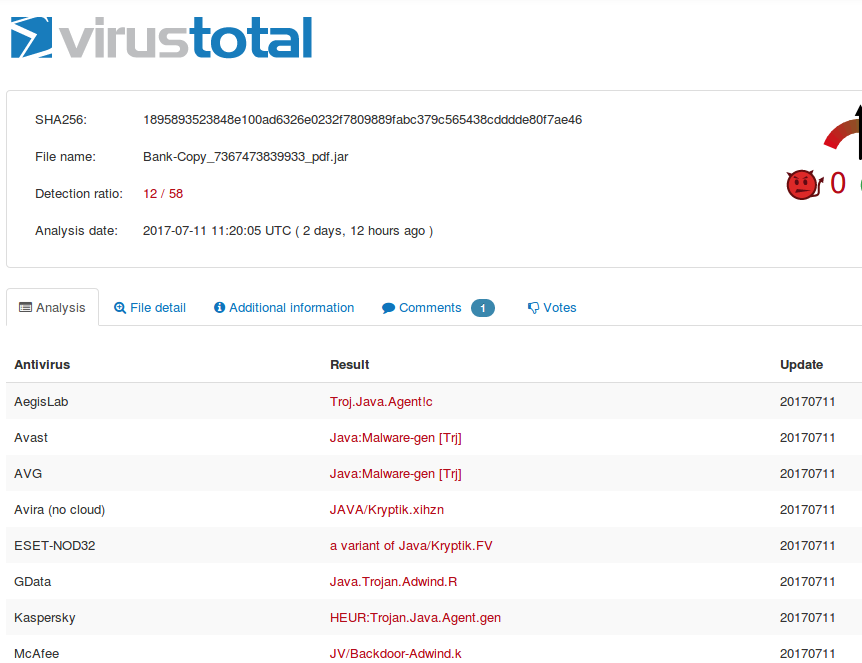
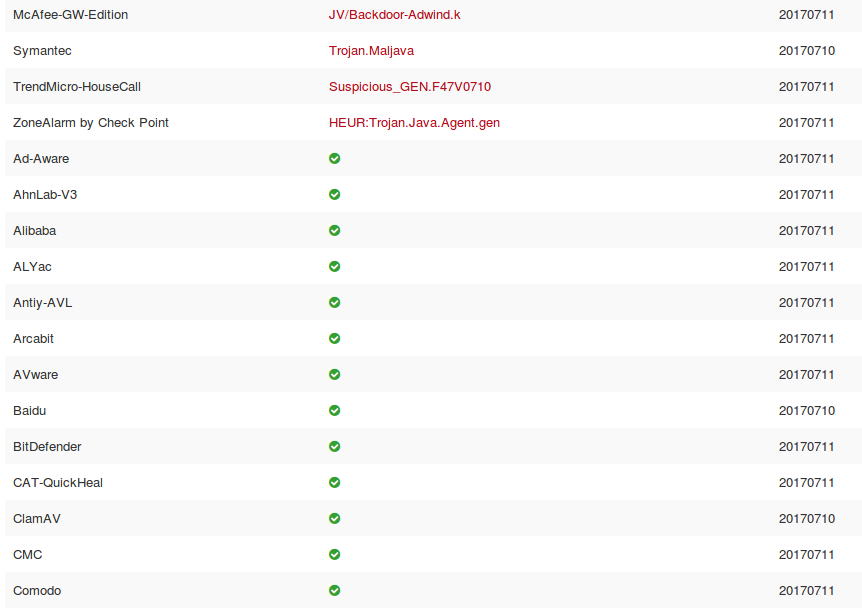
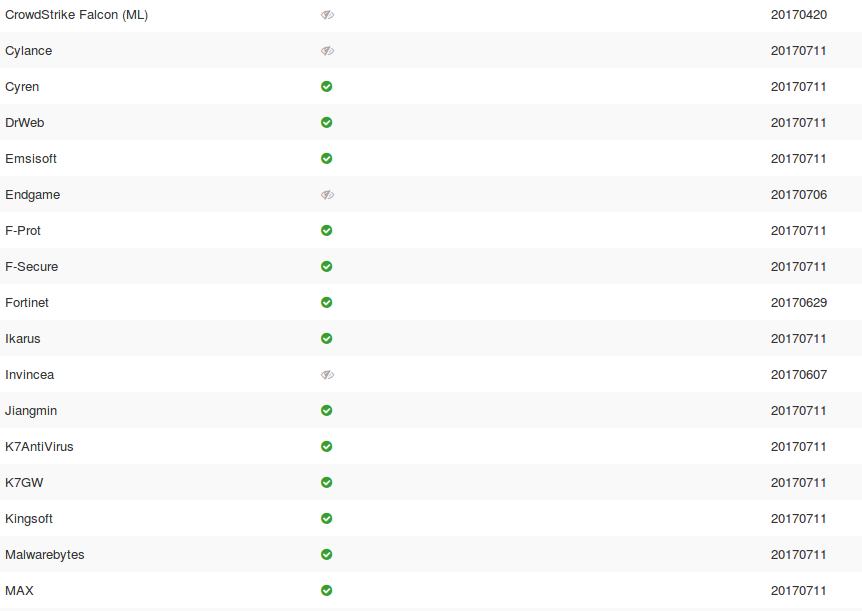
And here are screenshots of VirusTotal.com comparison analysis from 58 different AntiVirus program providers. Apparently many of them missed the Trojan.